Attacking & Exploitation
Before starting with this blog firstly visit wordpress enumeration blog .
Researchers discovered an ongoing malvertising (online advertising to spread malware.)campaign targeting millions of WordPress websites to infect with backdoor and exploiting the various WordPress plugins vulnerabilities.According to WordPress, there are nearly 60 million Websites power by WordPress content management system and hundreds of WordPress Plugins are installed that developers by various developers around the globe. Cyber criminals launch the payload by exploiting the vulnerabilities that reside in some of the most popular WordPress plugins and injecting malicious scripts in unpatched WordPress website.
Attacker: Kali Linux
Target: WordPress
Table Of Content
1.Brute-forcing wp-login.php form
2.Brute Force Login via xmlrpc.php
3.Denial of Service (DOS) via xmlrpc.php
4.Exploit WordPress Plugin
5.Exploit WordPress Theme Example
6.Sniff and Capture Credentials over non-secure login
7.Compromise Systems Administration Tools
8.Content Discovery
9.Vulnerable Server Software
1.Brute Force wp-login.php Form
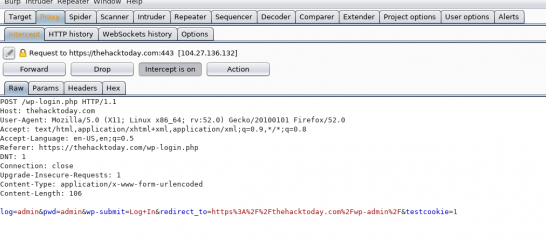
The most common attack against the WordPress user is brute forcing the password of an account to gain access to the back-end of the WordPress system. Other ways a password can be compromised include sniffing the password in clear text over a HTTP login session or even getting the credentials from a key logger on the workstation of the WordPress administrator.Accounts with administrator level access are the most sought after due to the amount of mischief an admin user can get up to; adding PHP command shells or malicious javascript directly through admin interface are common examples.
With the usernames we collected during information gathering we can get started (or just try admin). Take a look at the login form /wp-login.php, notice how failed logins confirm the username when an incorrect password is entered. This is very helpful to an attacker…. it also makes things more user friendly for the end user who has forgotten their username and password. This “feature” has been debated and it has been decided to keep this response within the WordPress code.
Brute forcing accounts of users is possible using a number of open source tools. In addition there are worm like scripts available that have spread through the WordPress ecosystem, searching for and spreading to WordPress sites with weak admin passwords.
WPScan
The previously mentioned WPScan tool in addition to enumeration, can also perform brute force login attacks.
wpscan --url example.com --wordlist /usr/share/wordlist/rockyou.txt --username testuser --threads 20
Nmap NSE Script
Nmap the port scanner can do much more than find open ports. Recent versions of Nmap come bundled with NSE scripts that can be used to test many different vulnerabilities; including enumerating users and brute forcing WordPress passwords.
nmap -sV --script http-wordpress-enum --script-args limit=25 example.com PORT STATE SERVICE REASON 80/tcp open http syn-ack | http-wordpress-enum: | Username found: admin | Username found: testadmin | Username found: fred | Username found: alice | Username found: bob |_Search stopped at ID #25. Increase the upper limit if necessary with 'http-wordpress-enum.limit'
Burp Suite
For those familiar with web application security testing, the Burp Suite Intruder tool can also be used for brute-forcing WordPress passwords. A WordPress login attempt is only a HTTP POST request after all.Configure Burp Intruder to send a valid username (or a list of usernames) along with a list of possible passwords and wait for the successful login.
2.Brute Force Login using xmlrpc.php
The xmlrpc.php capability is an API endpoint that allows mobile apps and other programmable access to backend functions of the WordPress site such as publishing posts. It is enabled by default and several attacks are possible against the endpoint depending on permissions and the version of the target WordPress installation.
By using the xmlrpc.php endpoint to attack WordPress accounts we may bypass security plugins that are protecting the login form from abuse. This password guessing attack may also be faster, with the result being you can attempt more passwords.
Notice the -d, in curl this is the data that is sent as part of the POST request. You could also use Burp or your favorite scripting language for this request.
curl -X POST -d "<methodCall><methodName>wp.getUsersBlogs</methodName><params><param><value>admin</value></param><param><value>pass</value></param></params></methodCall>" http://examplewp.com/xmlrpc.php
In the response we will see an invalid password response or success. It is easy to spot and work into your script.
3.Denial of Service (DOS) via xmlrpc.php
Another use of the xmlrpc.php endpoint is to perform a denial of service attack. If this capability is enabled, we can send a small request to the server and get it to respond with a full page of content to a target of our choosing. The idea is to make multiple requests from different systems and get them all to target a single host. Potentially knocking it offline due to network congestion.
First, we enumerate the capabilities of the xmlrpc.php endpoint.
curl -X POST -d "<methodCall><methodName>system.listMethods</methodName><params></params></methodCall>" http://examplewp.com/xmlrpc.php The response will be a list of available methods. <?xml version="1.0" encoding="UTF-8"?> <methodResponse> <params> <param> <value> <array><data> <value><string>system.listMethods</string></value> <value><string>system.getCapabilities</string></value> <value><string>pingback.extensions.getPingbacks</string></value> <value><string>pingback.ping</string></value> <value><string>mt.publishPost</string></value> **** truncated ****
Note the pingback.ping indicating pingback is enabled. Use the following data for the pingback attempt.
<methodCall> <methodName>pingback.ping</methodName> <params><param> <value><string>http://**denial-of-service-target**:**portno**</string></value> </param><param><value><string>http://**blog-url-from-wp**</string> </value></param></params> </methodCall>
Disabling access to xmlrpc.php from your web server or using .htaccess is recommended if you are not using the API. Not only will it block any attacks, it will reduce the amount of noise in your logs from the bots attempting to hit these API endpoints.
4.Exploit WordPress Plugin
Plugins, Themes and WordPress Core all contain a large amount of PHP code from developers around the world. These developers have differing abilities and focus when it comes to writing secure software. For this reason, there are thousands of exploitable vulnerabilities available to an attacker. Updating plugins, the WordPress core, and themes must be a routine task for any WordPress administrator to ensure the known vulnerabilities are patched.Common vulnerabilities include XSS, SQL injection, file upload, and code execution. All of these can have devastating consequences to a WordPress site. Search through Metasploit and exploit-db.com for exploitable WordPress bugs.
Revslider Example Exploit
An example of a WordPress plugin exploit is from a vulnerability discovered 5 years ago. The vulnerable revslider plugin resulted in tens of thousands of compromised WordPress sites. To this day, there are attempts to exploit it in our web server logs even in 2019. One reason it was such a popular plugin is that it was bundled with many themes.
A number of exploitation opportunities are possible, but this is perhaps the easiest to demonstrate. Exploitation is as difficult as loading this URL in a browser.
https://example.com/wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php
The HTTP request would download the wp-config.php file from the vulnerable site if it had the exploitable version of revslider installed. The exploit type is known as a local file include, as the attacker is tricking the application code into including a sensitive file in the output. The wp-config.php is not normally accessible and contains the database credentials for the WordPress database user.
With the database password, an attacker could attempt to login as the WordPress admin using the same password (if passwords were re-used). A more common attack vector would be to login to the phpmyadmin script, if installed, as this uses the database credentials. If MySQL is exposed, it may even possible to directly connect to the database using a MySQL database client and the leaked credentials.
Access to the database provides the attacker options to reset the administrator password, attempt to crack the admin hash, modify content in the database adding malicious js or iframes. There are many possibilities for further exploitation once the credentials in wp-config.php are leaked.
5.Exploit WordPress Theme Example
Exploits are available from various places and forums. This example uses an exploit from the popular Metasploit Exploitation Framework. The vulnerable theme is the very popular optimize press. The vulnerability was released back in 2013 and versions after 1.45 are not vulnerable to this exploit.Numerous bots and automated attack scripts that exploit WordPress sites do not perform the enumeration phase, they simply propel exploits at thousands of sites and hope for a successful payload.Plugins and themes not enabled can be exploited. Scanning for default locations of those vulnerable files is a highly common attack by automated bots.
![]()
6.Sniff and Capture Credentials over non-secure login
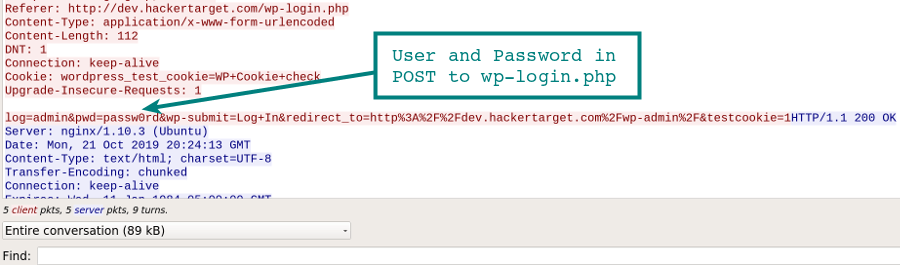
Without additional security measures in place (TLS/SSL), accessing the /wp-admin/ dashboard is over an unencrypted connection. This means if you log in to your WordPress site on an unsecured network, such as the wireless at your local coffee shop or airport, your login and password to manage the site could be captured by an attacker watching your session.
In this example Wireshark capture we can clearly see the username and password being captured in our POST request to wp-login.php.
7.Compromise Systems Administration Tools
A successful password guessing attack against a server management account will give an attacker full access to the server and the WordPress application.Services that can be attacked with brute force password guessing include:
>SSH Service >MySQL database service >Webmin Server Management >CPanel or WHCMS Web Hosting Control Panels >phpMyAdmin database management application
Reduce the chance of management account compromise:
>Use strong passwords everywhere, do not re-use them! >Move SSH to a different port >Use TLS/SSL for web based management services to prevent sniffing and credential compromise >White list IP addresses that are able to connect to Internet facing services
8.Content Discovery
Content Discovery is the process of attempting to find items of interest in a web path. It applies to any web application, but since we are attacking WordPress, target it towards typical files and paths of interest in a WordPress installation.
For example:
curl https://example.com/wp-config.php.bak curl https://example.com/.wp-config.php.swp
These two examples are using curl to find a possible backup file of the wp-config.php file that we discussed earlier, as it contains sensitive information including database credentials. The second attempt tries to download the backup file that vim automatically creates when it is editing a file. A good reason not to edit files directly on your production sites!
Using curl to perform this search task for hundreds or even thousands of common files could be accomplished with a little bit of scripting. On the other hand, more appropriate tools such as Burp Suite, or gobuster, a tool that is very fast due to its parallel processing, will do a much better job.
9.Vulnerable Server Software
Testing the WordPress application itself is only one part of ensuring your web site is secure. The server that hosts the website must also be kept secure.Exploitable security vulnerabilities can, of course, be present in server software or the operating system. Examples can be found on any vulnerability mailing list. Recently a remote code execution vulnerability was found in Exim one of the most popular mail delivery servers on the Internet. PHPMyAdmin is a popular application to attack, due to its popularity and a long list of vulnerabilities.
Server Software Misconfiguration
Even if no exploitable vulnerability is present, a simple misconfiguration can leave a service vulnerable. Often security vulnerabilities are introduced simply through a misconfiguration by an overworked system administrator.